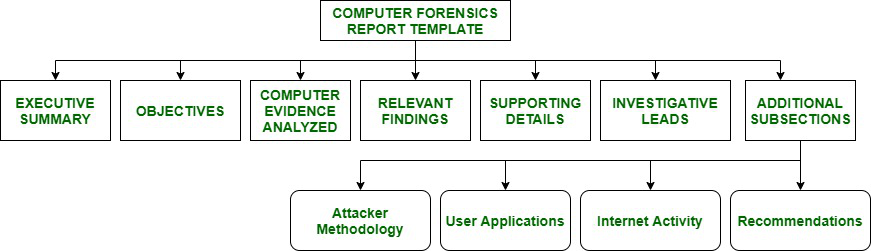
The main goal of Computer forensics is to perform a structured investigation on a computing device to find out what happened or who was responsible for what happened, while maintaining a proper documented chain of evidence in a formal report. Syntax or template of a Computer Forensic Report is as follows :

CAINE Linux stands for Computer Aided Investigative Environment. It is an Italian Linux live distribution, a digital forensics project that was started in 2008. It uses an old-school desktop environment complemented with top-notch specialty tools. In this article, we will discuss the following topics: What is CAINE? What is the Purpose behind the I
4 min read How to Create a Forensic Image with FTK Imager?A Forensic Image is most often needed to verify the integrity of the image after an acquisition of a Hard Drive has occurred. This is usually performed by law enforcement for court because, after a forensic image has been created, its integrity can be checked to verify that it has not been tampered with. Forensic Imaging is defined as the processes
5 min read What is Report Generator?A computer program is referred to as a report generator. The purpose of this computer program is to accept information or data from the database, spreadsheet, or XML stream which are the source, and then utilize the data for producing a structured composition satisfying the readership of a specific human. The process in which reports are made by us
3 min read How to Report Different Kinds of Phishing?Phishing is a major and vital issue with the aim of data stealing and security breaches in the network and is mostly used for targeting individuals, businesses, and organizations worldwide to get access to sensitive and touchy information. Phishing detection and reporting are very useful and must be followed to stay protected against cybercrime and
6 min read How to Find Network IP Address of Computer Using Computer Name?Answer: By using the command "ping" followed by the computer name in the command prompt or terminal.To find the network IP address of a computer using its computer name: Open Command Prompt or Terminal Begin by opening the Command Prompt (Windows) or Terminal (macOS/Linux) on your computer. Use the Ping Command Type "ping" followed by the computer
1 min read How To Connect One Computer To Another Computer via LAN?Answer: To connect one computer to another computer via LAN, use an Ethernet cable to directly connect their Ethernet ports.The most common methods include: Wired Ethernet Connection: Use an Ethernet cable to directly connect the two computers' network ports. For more than two computers, connect each computer to a network switch or router with Ethe
1 min read Difference between Micro Computer and Mini ComputerThe terms known as microcomputer and minicomputer may be confusing especially to those who started using computer parlance just a few times back. Both are names for distinct categories of computers which differ in size, performance, and purpose of their application. This article will provide a clear concept of Microcomputers and Minicomputers; this
7 min read Token Ring frame formatPrerequisite – Ethernet Frame Format Topology - Ring topology Transmission - Unidirectional Encoding - Differential Manchester encoding Access control - Token passing Data rates - 4 Mbps, 16 Mbps Token Ring Frame format: Start frame delimiter (SFD) - Alerts each station for the arrival of token(or data frame) or start of the frame. It is used to sy
2 min read IPv6 Addressing Format and ConventionsWe know that IPv4 addresses are mostly represented in a dotted decimal form like 192.168.10.1, and if written with a prefix mask then it would be written like 192.168.10.1/24, where /24 is the network mask. But IPv6 is long addressing format. IPv6 is 128 bit long and usually represented in hexadecimal format of addressing. IPv6 representation inclu
2 min read How to Format a Write–Protected Pen Drive?When you receive the error "The disk is write-protected", it means you tried formatting your Pendrive but were not able to. This may be due to external software or encryption that was probably used to lock the contents of the Pendrive and the contents within the drive are read-only. In this case, the computer does not allow you to format, edit, or
3 min read Link Access Procedure, Balanced (LAPB) Frame FormatLink Access Procedure, Balanced (LAPB) is basically a layer 2 protocol that is required in many control protocols like X.25. It was developed by ITU-T, OF Link Access Procedure (LAP) that itself comes from High-Level Data Link Control (HDLC). It runs at Layer 2 i.e. Data Link Layer (DLL) of the OSI Model. It is generally a balanced protocol that us
3 min read Point-to-Point Protocol (PPP) Frame FormatPoint-to-Point Protocol (PPP) is generally the default RAS protocol in Windows and is most commonly used protocol of data link layer that is required to encapsulate higher network-layer protocols simply to pass over synchronous and asynchronous communication lines. In PPP, link establishment is controlled and handled mainly by Link Control Protocol
3 min read Frame Format of BISYNCBinary Synchronous Communication Protocol (BISYNC) is a byte oriented communication protocol and a data link layer protocol, developed by IBM. In a byte oriented approach, every frame is viewed as a set of bytes/characters. Some of the favored byte oriented protocols are – BISYNC (Binary synchronous communications protocol) Point to point protocol
2 min read ARP Protocol Packet FormatPre-requisites: How Address Resolution Protocol (ARP) works? ARP is a communication mechanism that is used to translate a network address, such as an IP address, to a physical (MAC) address on a local network. ARP packets are transmitted and received on a network to achieve this mapping. An ARP packet's format, also known as an ARP packet header, h
2 min read TCP/IP Packet FormatTCP/IP's primary function is to transport computer data from one device to another. Different computer networks' protocols include TCP and IP. The primary contrast between TCP (Transmission Control Protocol) and IP (Internet Protocol) is the fundamental method by which it transmits the data. The basic difference in methodology is that IP functions
6 min read RARP Packet FormatReverse Address Resolution Protocol (RARP) is a networking protocol that is used to map a physical (MAC) address to an Internet Protocol (IP) address. It is used to obtain the IP address of a host based on its physical address. That is, it performs in a way that is exactly opposite to that of the ARP. RARP works in a very similar way to ARP but in
3 min read Format String Vulnerability and Prevention with ExampleA format string is an ASCII string that contains text and format parameters. Example: // A statement with format stringprintf("my name is : %s\n", "Akash");// Output// My name is : Akash There are several format strings that specify output in C and many other programming languages but our focus is on C. Format string vulnerabilities are a class of
3 min read Unicode Transformation FormatUnicode Transformation Format sometimes known as UTF, is a standardized technique for encoding written characters into digital form. This format specifies how Unicode characters will be converted into a sequence of bytes. The most common UTF forms are UTF-8, UTF-16, UTF-32 What is UTF?A Unicode Transformation Format or UTF is a standardized method
3 min read Ethernet Frame FormatThe basic frame format which is required for all MAC implementation is defined in IEEE 802.3 standard. Though several optional formats are being used to extend the protocol's basic capability. Ethernet frame starts with the Preamble and SFD, both work at the physical layer. The ethernet header contains both the Source and Destination MAC address, a
8 min read Computer Networks - GATE CSE Previous Year QuestionsSolving GATE Previous Year's Questions (PYQs) not only clears the concepts but also helps to gain flexibility, speed, accuracy, and understanding of the level of questions generally asked in the GATE exam, and that eventually helps you to gain good marks in the examination. Previous Year Questions help a candidate practice and revise for GATE, whic
4 min read Computer Networks | Set 5Following questions have been asked in GATE CS 2005 exam. 1) Packets of the same session may be routed through different paths in: (a) TCP, but not UDP (b) TCP and UDP (c) UDP, but not TCP (d) Neither TCP nor UDP Answer (b) Packet is the Network layer Protocol Data Unit (PDU). TCP and UDP are Transport layer protocols. Packets of same session may b
2 min read Computer Networks | Set 3Following Questions have been asked in GATE 2011 CS exam. 1) A layer-4 firewall ( a device that can look at all protocol headers up to the transport layer) CANNOT (A) block HTTP traffic during 9:00PM and 5:00AM (B) block all ICMP traffic (C) stop incoming traffic from a specific IP address but allow outgoing traffic to same IP (D) block TCP traffic
3 min read Computer Networks | Set 12Following questions have been asked in GATE CS 2009 exam. 1) Let G(x) be the generator polynomial used for CRC checking. What is the condition that should be satisfied by G(x) to detect odd number of bits in error? (A) G(x) contains more than two terms (B) G(x) does not divide 1+x^k, for any k not exceeding the frame length (C) 1+x is a factor of G
2 min read Computer Networks | Set 6Following questions have been asked in GATE CS 2005 exam. 1) An organization has a class B network and wishes to form subnets for 64 departments. The subnet mask would be: (a) 255.255.0.0 (b) 255.255.64.0 (c) 255.255.128.0 (d) 255.255.252.0 Answer (d) The size of network ID is 16 bit in class B networks. So bits after 16th bit must be used to creat
4 min read Computer Networks | Set 7Following questions have been asked in GATE CS 2008 exam. 1) Which of the following system calls results in the sending of SYN packets? (A) socket (B) bind (C) listen (D) connect Answer (D) socket() creates a new socket of a certain socket type, identified by an integer number, and allocates system resources to it. bind() is typically used on the s
3 min read Computer Networks | Set 8Following questions have been asked in GATE CS 2008 exam. 1) What is the maximum size of data that the application layer can pass on to the TCP layer below? (A) Any size (B) 2^16 bytes-size of TCP header (C) 2^16 bytes (D) 1500 bytes Answer (A) Application layer can send any size of data. There is no limit defined by standards. The lower layers div
2 min read Computer Networks | Set 9Following questions have been asked in GATE CS 2007 exam. 1) Which one of the following uses UDP as the transport protocol? (A) HTTP (B) Telnet (C) DNS (D) SMTP Answer (C) DNS primarily uses User Datagram Protocol (UDP) on port number 53 to serve requests. DNS queries consist of a single UDP request from the client followed by a single UDP reply fr
2 min read Computer Networks | Set 10Following questions have been asked in GATE CS 2007 exam. 1) The address of a class B host is to be split into subnets with a 6-bit subnet number. What is the maximum number of subnets and the maximum number of hosts in each subnet? (A) 62 subnets and 262142 hosts. (B) 64 subnets and 262142 hosts. (C) 62 subnets and 1022 hosts. (D) 64 subnets and 1
4 min read Computer Networks | Set 11Following questions have been asked in GATE CS 2006 exam. 1) Station A uses 32 byte packets to transmit messages to Station B using a sliding window protocol. The round trip delay between A and B is 80 milliseconds and the bottleneck bandwidth on the path between A and B is 128 kbps. What is the optimal window size that A should use? (A) 20 (B) 40
3 min read Computer Networks | IP Addressing | Question 5If subnet mask 255.255.255.224, which of the following will be Direct Broadcast address ? (A) 202.15.19.127 (B) 202.15.19.63 (C) Both a and b (D) None of the Above Answer: (C) Explanation: Subnet mask is 255.255.255.11100000 In DBA all host bits are 1. from option 202.15.19.011 11111 , this can be a DBA. 202.15.19.001 11111 ,this can also be a DB
1 min read Article Tags :